The Internet has drastically changed the way that children interact with the world. They have access to in-depth knowledge, tools to express their creativity, and people from all over the world. Yet along with offering a fascinating, new way to connect with the world, the Internet also offers new risks
Learning to recognize the warning signs of these risks will allow trusted adults to intervene and lessen potential negative impacts. By acting as a resource, parents and guardians can help make the Internet a safer place for their families. As a parent or guardian, you should stay well-informed about current issues to understand what your children are experiencing on and off the Internet. If they are social networking, instant messaging, using webcams, or blogging, help them use these tools safely by learning how to use them yourself. Children whose parents and guardians regularly talk to them about personal safety are more likely to exhibit responsible behavior on their own.
We invite you to learn about the most common issues surrounding your children’s online lives and begin a dialogue about safety with your children.
- Cyberbullying
- Exposure to inappropriate material
- Online predators
- Revealing too much personal information
Learning to recognize the warning signs of these risks will allow trusted adults to intervene and lessen potential negative impacts. By acting as a resource, parents and guardians can help make the Internet a safer place for their families. As a parent or guardian, you should stay well-informed about current issues to understand what your children are experiencing on and off the Internet. If they are social networking, instant messaging, using webcams, or blogging, help them use these tools safely by learning how to use them yourself. Children whose parents and guardians regularly talk to them about personal safety are more likely to exhibit responsible behavior on their own.
We invite you to learn about the most common issues surrounding your children’s online lives and begin a dialogue about safety with your children.

Blogging:
I don’t mean to be mean but I have had enough with homework. – Tween blogger
Do you ever wonder what your children think about? Perhaps you should read their Web logs or “blogs.” Blogs are a type of online journal that children use to share their thoughts and feelings; they may be in written or video format. Posting blogs allows children to develop both their technical and creative skills. It also lets them connect to other users with similar interests and write about their experiences, their personal lives, popular culture, and any other topic that crosses their minds.
If done safely, blogging can be a good exercise that encourages critical thinking and creative writing. Unfortunately, children sometimes forget their blogs are not private and share information not intended for outsiders. Then, there are those children who simply do not care if their information is public; the more eyes they attract, the better.
Risky Behavior Some blogs track the number of visitors and have places for their audiences to comment or rate them. As a result, children may engage in risky behavior—such as posting intimate details—in order to gain popularity on the Internet. Other risky behavior includes not using privacy settings, or posting inappropriate or illegal content.
These risky behaviors leave children open to being targeted by predators and cyberbullies. For example, a child’s peers may take information shared in a blog and use it to humiliate him at school. Likewise, a child sharing inappropriate content in a blog may find herself suspended from school or losing out on future educational opportunities. They might also find themselves approached by someone who intends them harm.
I don’t mean to be mean but I have had enough with homework. – Tween blogger
Do you ever wonder what your children think about? Perhaps you should read their Web logs or “blogs.” Blogs are a type of online journal that children use to share their thoughts and feelings; they may be in written or video format. Posting blogs allows children to develop both their technical and creative skills. It also lets them connect to other users with similar interests and write about their experiences, their personal lives, popular culture, and any other topic that crosses their minds.
If done safely, blogging can be a good exercise that encourages critical thinking and creative writing. Unfortunately, children sometimes forget their blogs are not private and share information not intended for outsiders. Then, there are those children who simply do not care if their information is public; the more eyes they attract, the better.
Risky Behavior Some blogs track the number of visitors and have places for their audiences to comment or rate them. As a result, children may engage in risky behavior—such as posting intimate details—in order to gain popularity on the Internet. Other risky behavior includes not using privacy settings, or posting inappropriate or illegal content.
These risky behaviors leave children open to being targeted by predators and cyberbullies. For example, a child’s peers may take information shared in a blog and use it to humiliate him at school. Likewise, a child sharing inappropriate content in a blog may find herself suspended from school or losing out on future educational opportunities. They might also find themselves approached by someone who intends them harm.

Cell Phones:
When you think about your children’s online activities, do you consider their cell phones? They have evolved from simple communication devices to mobile, miniature computers. For example, smartphones have operating systems similar to that of computers which allow users to download programs or “apps.” These apps help users do things like access e-mail and play games. Also, most cell phones allow users to download and upload content from the Internet just as they would on a computer. However, cell phones can be more difficult to monitor than a computer, and children often use them without adult supervision. Make sure to review your family’s Internet safety rules with your children and become aware of the following risks before allowing them to own cell phones
Making Cyberbullying More Painful
Cell phones make it easy for children to communicate with their friends, but they also make them vulnerable to cyberbullying. Cell phones can be used at anytime and anywhere, giving cyberbullies unlimited access to their victims. Children may send and receive mean-spirited phone calls, texts, and pictures at any hour.
Playing a Role in Grooming
Predators also know and take advantage of the fact that cell phones let them talk with their victims at any time. They are also aware that parents and guardians often forget to monitor children’s cell phones. Predators may send children cell phones and ask them to keep the phones a secret. They can then talk to and exchange text messages and pictures with children without close monitoring by parents and guardians. Others may ask children for their cell phone numbers after meeting them online or try to connect with willing children by sending texts to random numbers.
Sexting Made Easy
“Sexting” is a term used to describe the sending of sexually explicit text messages or pictures of minors by minors. What most young people do not realize is that the production, possession, and distribution of explicit photos of minors, even if they are self-produced, may be illegal. Furthermore, if these explicit photos end up on the Internet, children may be taunted by their peers and jeopardize scholastic, athletic, and employment opportunities.
Unintentional Sharing of Geolocation Data
Most smartphones have GPS technology which allows the user’s precise location to be pinpointed by apps and on websites. Social networking sites such as FourSquare, GoWalla, and Facebook take advantage of this technology by encouraging their users to “check-in” or share their locations. A “check-in” can be shared with a list of friends, so make sure you know who is on your child’s friends list before allowing them to use this type of technology. Children also may share their locations unintentionally through pictures taken with their smartphones; these photos often have geolocation data embedded in them. Consider disabling the location services on smartphones before allowing children to post photos online.
When you think about your children’s online activities, do you consider their cell phones? They have evolved from simple communication devices to mobile, miniature computers. For example, smartphones have operating systems similar to that of computers which allow users to download programs or “apps.” These apps help users do things like access e-mail and play games. Also, most cell phones allow users to download and upload content from the Internet just as they would on a computer. However, cell phones can be more difficult to monitor than a computer, and children often use them without adult supervision. Make sure to review your family’s Internet safety rules with your children and become aware of the following risks before allowing them to own cell phones
Making Cyberbullying More Painful
Cell phones make it easy for children to communicate with their friends, but they also make them vulnerable to cyberbullying. Cell phones can be used at anytime and anywhere, giving cyberbullies unlimited access to their victims. Children may send and receive mean-spirited phone calls, texts, and pictures at any hour.
Playing a Role in Grooming
Predators also know and take advantage of the fact that cell phones let them talk with their victims at any time. They are also aware that parents and guardians often forget to monitor children’s cell phones. Predators may send children cell phones and ask them to keep the phones a secret. They can then talk to and exchange text messages and pictures with children without close monitoring by parents and guardians. Others may ask children for their cell phone numbers after meeting them online or try to connect with willing children by sending texts to random numbers.
Sexting Made Easy
“Sexting” is a term used to describe the sending of sexually explicit text messages or pictures of minors by minors. What most young people do not realize is that the production, possession, and distribution of explicit photos of minors, even if they are self-produced, may be illegal. Furthermore, if these explicit photos end up on the Internet, children may be taunted by their peers and jeopardize scholastic, athletic, and employment opportunities.
Unintentional Sharing of Geolocation Data
Most smartphones have GPS technology which allows the user’s precise location to be pinpointed by apps and on websites. Social networking sites such as FourSquare, GoWalla, and Facebook take advantage of this technology by encouraging their users to “check-in” or share their locations. A “check-in” can be shared with a list of friends, so make sure you know who is on your child’s friends list before allowing them to use this type of technology. Children also may share their locations unintentionally through pictures taken with their smartphones; these photos often have geolocation data embedded in them. Consider disabling the location services on smartphones before allowing children to post photos online.

Children As Victims
In order to help protect children from online sexual predators, it is important that parents and guardians understand how children’s vulnerabilities may make them susceptible to manipulation by these predators.
Curiosity Children are naturally curious about sex. By acting as guides, predators can exploit this curiosity and gradually lure children into sexual activity. Adolescents questioning their sexuality are even more at risk, as they may go online with the intent of finding support and companionship. Instead, they may find adults looking to take advantage of this vulnerability.
Need for Attention Even if children receive ample attention from their families, they still crave it from others, especially those they perceive as older and more mature. Predators may offer children affection and flattery in order to coerce them into sexual acts.
Rebellion Children may become rebellious when they reach adolescence, and predators can use this to their advantage. A child who is victimized while disobeying parental rules may be reluctant to admit it for fear of being punished.
Respect for Adults Because children are taught to obey and respect adults, they may be less likely to disobey directions given by an adult, even those which make them uncomfortable. An adult looking to harm children can exploit this to influence a child’s behavior.
In order to help protect children from online sexual predators, it is important that parents and guardians understand how children’s vulnerabilities may make them susceptible to manipulation by these predators.
Curiosity Children are naturally curious about sex. By acting as guides, predators can exploit this curiosity and gradually lure children into sexual activity. Adolescents questioning their sexuality are even more at risk, as they may go online with the intent of finding support and companionship. Instead, they may find adults looking to take advantage of this vulnerability.
Need for Attention Even if children receive ample attention from their families, they still crave it from others, especially those they perceive as older and more mature. Predators may offer children affection and flattery in order to coerce them into sexual acts.
Rebellion Children may become rebellious when they reach adolescence, and predators can use this to their advantage. A child who is victimized while disobeying parental rules may be reluctant to admit it for fear of being punished.
Respect for Adults Because children are taught to obey and respect adults, they may be less likely to disobey directions given by an adult, even those which make them uncomfortable. An adult looking to harm children can exploit this to influence a child’s behavior.

Cyberbullying:
Cyberbullying is just what it sounds like - bullying through Internet applications and technologies such as instant messaging (IM), social networking sites, and cell phones. It can start easily—with a rumor, a photo, or a forwarded message—and just as easily spiral out of control. An embarrassing video posted to a social networking site by someone in Kansas tonight may be watched by someone in Japan tomorrow. Cyberbullying victims may be targeted anywhere, at any time.
Common Forms of Cyberbullying:
Cyberbullying is just what it sounds like - bullying through Internet applications and technologies such as instant messaging (IM), social networking sites, and cell phones. It can start easily—with a rumor, a photo, or a forwarded message—and just as easily spiral out of control. An embarrassing video posted to a social networking site by someone in Kansas tonight may be watched by someone in Japan tomorrow. Cyberbullying victims may be targeted anywhere, at any time.
Common Forms of Cyberbullying:
- Flaming and Trolling – sending or posting hostile messages intended to “inflame” the emotions of others
- Happy-Slapping – recording someone being harassed or bullied in a way that usually involves physical abuse, then posting the video online for public viewing
- Identity Theft/Impersonation – stealing someone’s password and/or hijacking their online accounts to send or post incriminating or humiliating pictures, videos, or information
- Photoshopping – doctoring digital images so that the main subject is placed in a compromising or embarrassing situation
- Physical Threats – sending messages that involve threats to a person’s physical safety
- Rumor Spreading – spreading gossip through e-mail, text messaging, or social networking sites
- Avoids the computer, cell phone, and other technological devices or appears stressed when receiving an e-mail, instant message, or text
- Withdraws from family and friends or acts reluctant to attend school and social events
- Avoids conversations about computer use
- Exhibits signs of low self-esteem including depression and/or fear
- Has declining grades
- Has poor eating or sleeping habits

E-mail, IM & Chat Rooms:
A study from the Pew Internet & American Life Project shows that teens (ages 12-17) use text messaging to communicate with their friends more than e-mail or instant messaging (IM). However, these online communication services, along with chat rooms, continue to be an important part of children’s online interactions. E-mail accounts, for example, are often necessary to join social networking sites, online games, and virtual worlds. Social networking sites, like Facebook, often have IM and e-mail components.
E-mail, IM, and chat room programs let children communicate with friends and family members. They can also allow children to connect with people that they have never met in person, making them vulnerable to online predators, cyberbullies, and scam artists. Knowing a little about each of these communication services, and the associated risks, can help parents, guardians, and other trusted adults keep children safer while online.
E-mail
Through e-mail, users can easily send and receive messages. These messages may also have text, audio, and picture files attached. Signing up for an e-mail account is simple, as most services offer them for free and do not check the identities of users. This allows cyberbullies or scam artists to anonymously send harassing messages or spam. Sometimes these messages contain viruses, scams, or other inappropriate content, so trusted adults should warn children to be wary of e-mails from unknown people.
Instant Messaging
Instant messaging programs allow users to exchange real-time messages with people from a list of contacts, also known as a “buddy” list. Children may not know the true identities of their buddies, as IM accounts can be acquired anonymously. Trusted adults should review children’s buddy lists for unknown contacts, and talk to them about the identities of the people on the lists. Trusted adults should also learn some of the chat acronyms, such as POS (parent over shoulder) and A/S/L (age/sex/location), which children use to communicate over IM. This will help you be aware of anyone saying anything inappropriate to your child.
Chat Rooms
Chat rooms are online hang-out spots where anyone can talk about anything—current events, books, and other common interests. Users often do not know each other in real life, so it is important that trusted adults keep a close eye on the content of any conversations.
Chat rooms offer features which allow users to chat through private, one-on-one messages. Predators may use this to entice children into conversations about sex and offline meetings. Parents and guardians should be aware of secretive behavior, such as a child minimizing the screen when an adult enters the room.
A study from the Pew Internet & American Life Project shows that teens (ages 12-17) use text messaging to communicate with their friends more than e-mail or instant messaging (IM). However, these online communication services, along with chat rooms, continue to be an important part of children’s online interactions. E-mail accounts, for example, are often necessary to join social networking sites, online games, and virtual worlds. Social networking sites, like Facebook, often have IM and e-mail components.
E-mail, IM, and chat room programs let children communicate with friends and family members. They can also allow children to connect with people that they have never met in person, making them vulnerable to online predators, cyberbullies, and scam artists. Knowing a little about each of these communication services, and the associated risks, can help parents, guardians, and other trusted adults keep children safer while online.
Through e-mail, users can easily send and receive messages. These messages may also have text, audio, and picture files attached. Signing up for an e-mail account is simple, as most services offer them for free and do not check the identities of users. This allows cyberbullies or scam artists to anonymously send harassing messages or spam. Sometimes these messages contain viruses, scams, or other inappropriate content, so trusted adults should warn children to be wary of e-mails from unknown people.
Instant Messaging
Instant messaging programs allow users to exchange real-time messages with people from a list of contacts, also known as a “buddy” list. Children may not know the true identities of their buddies, as IM accounts can be acquired anonymously. Trusted adults should review children’s buddy lists for unknown contacts, and talk to them about the identities of the people on the lists. Trusted adults should also learn some of the chat acronyms, such as POS (parent over shoulder) and A/S/L (age/sex/location), which children use to communicate over IM. This will help you be aware of anyone saying anything inappropriate to your child.
Chat Rooms
Chat rooms are online hang-out spots where anyone can talk about anything—current events, books, and other common interests. Users often do not know each other in real life, so it is important that trusted adults keep a close eye on the content of any conversations.
Chat rooms offer features which allow users to chat through private, one-on-one messages. Predators may use this to entice children into conversations about sex and offline meetings. Parents and guardians should be aware of secretive behavior, such as a child minimizing the screen when an adult enters the room.

File Sharing:
Peer-to-peer (P2P) file-sharing services allow users to upload their files so that other people can download them. It can be an easy way for people to share photos, videos, and other content. Unfortunately, it has also turned into an easy way for people to illegally share copyrighted materials such as movies, software, music, and even illegal materials, like child pornography. Illegally downloading software content from the Web is called piracy.
Piracy Children do not always understand that piracy is stealing because they are not physically going to a store, taking something off the shelf, and leaving without paying for it. Instead, they are sitting at home on their own computer and downloading or uploading copyrighted movies, music, and software. If caught, parents or guardians may be held responsible for their child’s piracy, resulting in a financial penalty or worse.
Security In addition to the legality issue, there are security concerns. Files may be intentionally mislabeled in order to disguise viruses, pornography, and other unwanted content. Some file-sharing programs require the user to download a program or “plug-in,” which may come packaged with hidden spyware. Unfortunately, most P2P services do not have a central Web server where complaints may be filed. Therefore, it is important that parents and guardians pay careful attention to what their children download through file-sharing services. Make sure to scan all downloaded files for viruses and other malware, and look at all of your child’s downloaded files to ensure that the content is what was expected.
Peer-to-peer (P2P) file-sharing services allow users to upload their files so that other people can download them. It can be an easy way for people to share photos, videos, and other content. Unfortunately, it has also turned into an easy way for people to illegally share copyrighted materials such as movies, software, music, and even illegal materials, like child pornography. Illegally downloading software content from the Web is called piracy.
Piracy Children do not always understand that piracy is stealing because they are not physically going to a store, taking something off the shelf, and leaving without paying for it. Instead, they are sitting at home on their own computer and downloading or uploading copyrighted movies, music, and software. If caught, parents or guardians may be held responsible for their child’s piracy, resulting in a financial penalty or worse.
Security In addition to the legality issue, there are security concerns. Files may be intentionally mislabeled in order to disguise viruses, pornography, and other unwanted content. Some file-sharing programs require the user to download a program or “plug-in,” which may come packaged with hidden spyware. Unfortunately, most P2P services do not have a central Web server where complaints may be filed. Therefore, it is important that parents and guardians pay careful attention to what their children download through file-sharing services. Make sure to scan all downloaded files for viruses and other malware, and look at all of your child’s downloaded files to ensure that the content is what was expected.

Gaming:
Some parents and guardians think that online games are simply a form of entertainment. However, children also have the chance to exercise important life skills while gaming. They may use their imaginations and employ problem-solving strategies to overcome obstacles. They may also practice their social skills through online interactions with other gamers.
Using instant chat features, forums, and voice-enabled interactions, children can communicate and collaborate with gamers all over the world. Unfortunately, these features can also expose children to people who may not have their best interests in mind.
Risks of Gaming
Many online games have communication features which allow their users to interact anonymously. Some people may take advantage of this anonymity to target children. For example, predators may send inappropriate content or use a game’s communication functions to arrange in-person meetings. Cyberbullies may harass fellow gamers and online scam artists may promise virtual goods in an effort to get credit card information.
Some game consoles allow Internet access as well, so it is important to be aware of their communication features. Predators have sent children inappropriate content through game consoles in attempts to coax them into reciprocating or meeting offline.
Some parents and guardians think that online games are simply a form of entertainment. However, children also have the chance to exercise important life skills while gaming. They may use their imaginations and employ problem-solving strategies to overcome obstacles. They may also practice their social skills through online interactions with other gamers.
Using instant chat features, forums, and voice-enabled interactions, children can communicate and collaborate with gamers all over the world. Unfortunately, these features can also expose children to people who may not have their best interests in mind.
Risks of Gaming
Many online games have communication features which allow their users to interact anonymously. Some people may take advantage of this anonymity to target children. For example, predators may send inappropriate content or use a game’s communication functions to arrange in-person meetings. Cyberbullies may harass fellow gamers and online scam artists may promise virtual goods in an effort to get credit card information.
Some game consoles allow Internet access as well, so it is important to be aware of their communication features. Predators have sent children inappropriate content through game consoles in attempts to coax them into reciprocating or meeting offline.

Identity Theft:
Millions of Americans use the Internet to make their lives more convenient by shopping and banking online. Unfortunately, the personal information that they share—anything from credit card to Social Security numbers—may expose them to identity theft.
Methods According to the Federal Trade Commission (FTC), identity thieves can obtain information by rummaging through trash or stealing from purses, wallets, mailboxes, or homes.[1] They may also use electronic methods, such as those listed below.
Once identity thieves obtain a victim’s personal information, they may use it to run up charges on credit cards, open additional accounts, take out loans, lease property, or apply for a driver’s license. Fortunately, by changing just a few habits, you can help protect yourself and your family from becoming victims of identity theft.
Protecting Yourself: The number one rule when it comes to protecting yourself from identity theft is pay attention! Many online scams depend on you being fooled by false websites, spam, and offers. Minimize the chance that you will be taken advantage of by closely examining any site that asks for your personal information. For example, look for “https” or a lock symbol in the address bar when making purchases online. This means that you are viewing a secure Web page with the necessary allocations for privacy and protection.
You should also talk to your children about online scamming techniques. Warn them about clicking on pop-ups and downloading programs from unknown sources, as these may be tricks to install malware or get personal information. Also, make sure to have antivirus software and firewall programs installed on your computer. Although these programs are not always infallible, they are essential in helping to keep your personal information private and your computer working properly.
Responding to Identity Theft: Checking your account statements and credit card reports frequently will give you the advantage when it comes to responding to identity theft. If you suspect that you have been a victim of identity theft, file a report with your local law-enforcement agency and the FTC, and place a fraud alert on your credit reports. Promptly close any compromised accounts.
Millions of Americans use the Internet to make their lives more convenient by shopping and banking online. Unfortunately, the personal information that they share—anything from credit card to Social Security numbers—may expose them to identity theft.
Methods According to the Federal Trade Commission (FTC), identity thieves can obtain information by rummaging through trash or stealing from purses, wallets, mailboxes, or homes.[1] They may also use electronic methods, such as those listed below.
- Phishing relies on pop-ups, spam, and websites that look authentic to obtain personal information, such as log-in information and credit card numbers.
- Pharming uses malicious code to redirect users to fraudulent sites where hackers can access their personal information.
- Pretexting acquires personal information through false and illegal means, for example, obtaining financial information by pretending to call from a bank.
Once identity thieves obtain a victim’s personal information, they may use it to run up charges on credit cards, open additional accounts, take out loans, lease property, or apply for a driver’s license. Fortunately, by changing just a few habits, you can help protect yourself and your family from becoming victims of identity theft.
Protecting Yourself: The number one rule when it comes to protecting yourself from identity theft is pay attention! Many online scams depend on you being fooled by false websites, spam, and offers. Minimize the chance that you will be taken advantage of by closely examining any site that asks for your personal information. For example, look for “https” or a lock symbol in the address bar when making purchases online. This means that you are viewing a secure Web page with the necessary allocations for privacy and protection.
You should also talk to your children about online scamming techniques. Warn them about clicking on pop-ups and downloading programs from unknown sources, as these may be tricks to install malware or get personal information. Also, make sure to have antivirus software and firewall programs installed on your computer. Although these programs are not always infallible, they are essential in helping to keep your personal information private and your computer working properly.
Responding to Identity Theft: Checking your account statements and credit card reports frequently will give you the advantage when it comes to responding to identity theft. If you suspect that you have been a victim of identity theft, file a report with your local law-enforcement agency and the FTC, and place a fraud alert on your credit reports. Promptly close any compromised accounts.

Inappropriate Content:
In many ways the Internet is like a gigantic library; both have content to teach and entertain. And similar to the content in a library, not all Internet content is appropriate for children. Libraries create children’s and young adults’ sections in order to help youths (and their parents) identify which materials are appropriate for them. On the Internet, however, all of the content may be equally accessible; websites about ponies and websites featuring pornography are both a click away.
Sexually Explicit Material
Sexually explicit material, such as legal adult pornography and illegal child pornography, are readily available online. Consequently, many young people are learning about sex from the Internet, media, or their peers. According to developmental pediatrician Dr. Sharon Cooper, “The more often a person is exposed to potentially harmful materials, the more normal it seems and the more desensitized the person becomes.”[1] Without the counsel of parents and guardians, children may develop flawed views and opinions of their self-image and sexuality, which could affect their development.
Other Inappropriate Content
In addition to sexual content, children may be exposed to materials which glorify risky and illegal behaviors, making teens think it is “cool” to copy these activities. For example, some sites offer text or video instructions on anything from picking locks to playing alcoholic drinking games to making bombs. Other sites encourage dangerous behaviors such as cutting, anorexia, and suicide and may even have tips about how to hide the behaviors from family and friends. Children do not have to look hard to find inappropriate content; it is as easy as typing a word into the search bar on Google. Even blocking, filtering, and monitoring software can be overcome by a determined child. A child may also accidently click the wrong link or misspell a Web address and be led to websites with inappropriate content. That is why when it comes to dealing with inappropriate material, adult guidance and supervision are key.
In many ways the Internet is like a gigantic library; both have content to teach and entertain. And similar to the content in a library, not all Internet content is appropriate for children. Libraries create children’s and young adults’ sections in order to help youths (and their parents) identify which materials are appropriate for them. On the Internet, however, all of the content may be equally accessible; websites about ponies and websites featuring pornography are both a click away.
Sexually Explicit Material
Sexually explicit material, such as legal adult pornography and illegal child pornography, are readily available online. Consequently, many young people are learning about sex from the Internet, media, or their peers. According to developmental pediatrician Dr. Sharon Cooper, “The more often a person is exposed to potentially harmful materials, the more normal it seems and the more desensitized the person becomes.”[1] Without the counsel of parents and guardians, children may develop flawed views and opinions of their self-image and sexuality, which could affect their development.
Other Inappropriate Content
In addition to sexual content, children may be exposed to materials which glorify risky and illegal behaviors, making teens think it is “cool” to copy these activities. For example, some sites offer text or video instructions on anything from picking locks to playing alcoholic drinking games to making bombs. Other sites encourage dangerous behaviors such as cutting, anorexia, and suicide and may even have tips about how to hide the behaviors from family and friends. Children do not have to look hard to find inappropriate content; it is as easy as typing a word into the search bar on Google. Even blocking, filtering, and monitoring software can be overcome by a determined child. A child may also accidently click the wrong link or misspell a Web address and be led to websites with inappropriate content. That is why when it comes to dealing with inappropriate material, adult guidance and supervision are key.

Predators:
Although the Internet did not create child predators, it has significantly increased the opportunities predators have to meet victims while minimizing detection. They can communicate with children anonymously through instant messaging, social networking sites, chat rooms, message boards, and even cell phones.
Online predators do not fit any one mold or stereotype; seemingly upstanding citizens have been caught enticing children for sexual acts. Contrary to popular belief, most online predators are not pedophiles. Pedophiles target pre-pubescent children, while online predators typically target adolescents who engage in risky online behavior.
Grooming Predators take advantage of children’s natural vulnerabilities, such as their desire to appear adult or their need for attention. “Grooming” is the process through which predators play on these vulnerabilities by offering children gifts and attention.
It does not happen overnight. Grooming can be a long process that a patient, tenacious predator has planned and perfected to gain a child’s trust. This grooming may lead to the child’s willingness to meet the person with whom he or she is chatting. Offenders will often entice a child into a face-to-face meeting by
Warning Signs of Grooming or Exploitation in your Child
Although the Internet did not create child predators, it has significantly increased the opportunities predators have to meet victims while minimizing detection. They can communicate with children anonymously through instant messaging, social networking sites, chat rooms, message boards, and even cell phones.
Online predators do not fit any one mold or stereotype; seemingly upstanding citizens have been caught enticing children for sexual acts. Contrary to popular belief, most online predators are not pedophiles. Pedophiles target pre-pubescent children, while online predators typically target adolescents who engage in risky online behavior.
Grooming Predators take advantage of children’s natural vulnerabilities, such as their desire to appear adult or their need for attention. “Grooming” is the process through which predators play on these vulnerabilities by offering children gifts and attention.
It does not happen overnight. Grooming can be a long process that a patient, tenacious predator has planned and perfected to gain a child’s trust. This grooming may lead to the child’s willingness to meet the person with whom he or she is chatting. Offenders will often entice a child into a face-to-face meeting by
- Exploiting a child’s natural curiosity about sex
- Lowering the child’s inhibitions by gradually introducing explicit images and child sex abuse images
- Using his or her adult status to influence and control a child’s behavior
- Offering attention and affection
- Betraying a child’s trust by manipulating his or her emotions and insecurities
Warning Signs of Grooming or Exploitation in your Child
- Spends an excessive amount of time on the computer
- Becomes angry when he or she cannot get on the computer
- Withdraws from family and friends
- Minimizes the screen or turns off the monitor when you come into the room
- Inappropriate images or websites on the computer
- Strange phone numbers on your telephone bill
- Gifts in the mail from someone you don’t know, such as webcams or cell phones

Revealing Too Much:
Web 2.0 lets users share information online as easily as they download it. Unfortunately, people of all ages often reveal too much. Children can be made especially vulnerable by sharing personal information, such as home addresses and phone numbers, private thoughts and feelings, and pictures. In order to keep your children from posting information and images they may end up regretting, remind them who may see the information they reveal while online.
Predators are always looking to collect information about their child victims. This information may be used to identify, connect with, or manipulate children. For example, if a child blogs about being misunderstood, a predator might provide a sympathetic ear in order to create trust and form a relationship. Predators may also try to encourage children into a sexual relationship by talking about sex, so children should avoid talking about provocative subjects with people they do not know.
Cyberbullies take their targets’ personal information and use it against them. They may copy and alter photos; share private e-mail or instant message conversations; and taunt their victims with emotional insecurities revealed in blogs.
Scammers want to use children’s personal information to manipulate them. Children who post e-mail addresses and phone numbers may be the targets of spam, telemarketers, and e-mail scams.
It is also becoming more common for coaches, college admissions officers, and employers to screen applicants by checking their online profiles and postings. An admissions officer’s decisions may be negatively influenced by a teen’s posts - for example, rude comments about teachers or inappropriate photos.
Web 2.0 lets users share information online as easily as they download it. Unfortunately, people of all ages often reveal too much. Children can be made especially vulnerable by sharing personal information, such as home addresses and phone numbers, private thoughts and feelings, and pictures. In order to keep your children from posting information and images they may end up regretting, remind them who may see the information they reveal while online.
Predators are always looking to collect information about their child victims. This information may be used to identify, connect with, or manipulate children. For example, if a child blogs about being misunderstood, a predator might provide a sympathetic ear in order to create trust and form a relationship. Predators may also try to encourage children into a sexual relationship by talking about sex, so children should avoid talking about provocative subjects with people they do not know.
Cyberbullies take their targets’ personal information and use it against them. They may copy and alter photos; share private e-mail or instant message conversations; and taunt their victims with emotional insecurities revealed in blogs.
Scammers want to use children’s personal information to manipulate them. Children who post e-mail addresses and phone numbers may be the targets of spam, telemarketers, and e-mail scams.
It is also becoming more common for coaches, college admissions officers, and employers to screen applicants by checking their online profiles and postings. An admissions officer’s decisions may be negatively influenced by a teen’s posts - for example, rude comments about teachers or inappropriate photos.

Sexting:
When teenagers ask for cell phones, they usually want the coolest, trendiest cell phone on the market. These days, that phone will have photo and video capabilities. Put that together with the unlimited text messaging plan that your teen is sure to beg for and here comes possible trouble. Silly photos and embarrassing videos aside, cameras and texting have given young people a new and potentially dangerous way to explore their curiosity: sexting.
When teenagers ask for cell phones, they usually want the coolest, trendiest cell phone on the market. These days, that phone will have photo and video capabilities. Put that together with the unlimited text messaging plan that your teen is sure to beg for and here comes possible trouble. Silly photos and embarrassing videos aside, cameras and texting have given young people a new and potentially dangerous way to explore their sexuality: sexting.
What is sexting?
Sexting is the exchange of sexually suggestive messages or images between minors via cell phone. For example, a girl might take a nude picture of herself and send it to her boyfriend. Her boyfriend may forward the picture to one or two friends, who then decide to forward the picture to others. In this way, the girl’s picture could travel all over the Web, amassing countless viewers in a very short period of time. Please note that sexting does not include situations in which young people are coerced or blackmailed into sending sexually explicit images of themselves to adults. These adults are predators and the incident should be reported to law enforcement immediately.
Understanding teens and sexting
The majority of teens are actually not sexting: according to a study from the Pew American Life & Internet Project, only 4% of cell-owning teens (12-17) say they have sent nude or partially nude images[1]. Teens that are sexting often do so within the context of a relationship. A teen may send a sexual image to someone to indicate his or her interest in starting a romantic relationship. Or teens already in romantic relationships may sext each other as a prelude to or as part of a sexual relationship. Teens may also use sexting as a way of exploring their sexuality[2].
Some teens have been coerced into sexting when a boyfriend or girlfriend makes it a requirement for continuing their relationship. Others have been blackmailed into sharing nude photos by threats to expose previously taken nude pictures. When discussing sexting with your children, talk to them about the importance of bringing any such threats to you rather than trying to handle them on their own so that you may get law enforcement involved immediately.
Sexting consequences
When teens sext, they may not think about the consequences of their images becoming public. If an image surfaces at school, its creator and anyone caught distributing or possessing it may face removal from athletic teams or student groups and suspension. If a sexting incident involves harassment, coercion, or images passed around without the creator’s permission, law enforcement may become involved. Teens are unlikely to be charged with a serious crime for sexting, but they may be ordered to attend educational programs or complete community service. In addition to these consequences, the image’s creator may face additional emotional and psychological stressors, such as bullying and harassment by peers and judgment by friends and family. Some teens have moved schools or started attending homeschool to try to get a fresh start; unfortunately, sexting images can easily follow teens, victimizing them again. Sexting photos may even resurface years later during online searches by college admissions officers, employers, friends, and significant others. The images may also find their way into the hands of online sexual predators and be passed around for years after the teen has become an adult.
When teenagers ask for cell phones, they usually want the coolest, trendiest cell phone on the market. These days, that phone will have photo and video capabilities. Put that together with the unlimited text messaging plan that your teen is sure to beg for and here comes possible trouble. Silly photos and embarrassing videos aside, cameras and texting have given young people a new and potentially dangerous way to explore their curiosity: sexting.
When teenagers ask for cell phones, they usually want the coolest, trendiest cell phone on the market. These days, that phone will have photo and video capabilities. Put that together with the unlimited text messaging plan that your teen is sure to beg for and here comes possible trouble. Silly photos and embarrassing videos aside, cameras and texting have given young people a new and potentially dangerous way to explore their sexuality: sexting.
What is sexting?
Sexting is the exchange of sexually suggestive messages or images between minors via cell phone. For example, a girl might take a nude picture of herself and send it to her boyfriend. Her boyfriend may forward the picture to one or two friends, who then decide to forward the picture to others. In this way, the girl’s picture could travel all over the Web, amassing countless viewers in a very short period of time. Please note that sexting does not include situations in which young people are coerced or blackmailed into sending sexually explicit images of themselves to adults. These adults are predators and the incident should be reported to law enforcement immediately.
Understanding teens and sexting
The majority of teens are actually not sexting: according to a study from the Pew American Life & Internet Project, only 4% of cell-owning teens (12-17) say they have sent nude or partially nude images[1]. Teens that are sexting often do so within the context of a relationship. A teen may send a sexual image to someone to indicate his or her interest in starting a romantic relationship. Or teens already in romantic relationships may sext each other as a prelude to or as part of a sexual relationship. Teens may also use sexting as a way of exploring their sexuality[2].
Some teens have been coerced into sexting when a boyfriend or girlfriend makes it a requirement for continuing their relationship. Others have been blackmailed into sharing nude photos by threats to expose previously taken nude pictures. When discussing sexting with your children, talk to them about the importance of bringing any such threats to you rather than trying to handle them on their own so that you may get law enforcement involved immediately.
Sexting consequences
When teens sext, they may not think about the consequences of their images becoming public. If an image surfaces at school, its creator and anyone caught distributing or possessing it may face removal from athletic teams or student groups and suspension. If a sexting incident involves harassment, coercion, or images passed around without the creator’s permission, law enforcement may become involved. Teens are unlikely to be charged with a serious crime for sexting, but they may be ordered to attend educational programs or complete community service. In addition to these consequences, the image’s creator may face additional emotional and psychological stressors, such as bullying and harassment by peers and judgment by friends and family. Some teens have moved schools or started attending homeschool to try to get a fresh start; unfortunately, sexting images can easily follow teens, victimizing them again. Sexting photos may even resurface years later during online searches by college admissions officers, employers, friends, and significant others. The images may also find their way into the hands of online sexual predators and be passed around for years after the teen has become an adult.
Social Networking:
Social networking sites (SNS) such as MySpace, Facebook, Bebo, and Twitter are popular with teens because they give them
SNS Basics Although not every social networking site has all of these components, many of them add more and more features in an effort to keep users on their sites for longer periods of time. Instead of opening multiple applications, users can rely on one SNS to serve all their communications needs.
Social networking sites (SNS) such as MySpace, Facebook, Bebo, and Twitter are popular with teens because they give them
- An easy way to share their lives with their friends and family
- The chance to try on different identities and explore new interests
- A semi-private platform on which to communicate outside of the supervision of adults
SNS Basics Although not every social networking site has all of these components, many of them add more and more features in an effort to keep users on their sites for longer periods of time. Instead of opening multiple applications, users can rely on one SNS to serve all their communications needs.
- Blogs – These online journals or diaries are becoming a common part of many SNS.
- Comment Walls – A popular feature of most SNS that allows users to communicate through comments left on each others’ pages.
- E-mail – Most SNS have an e-mail feature through which users can communicate privately or with select groups.
- Friends Lists – These contact lists are usually comprised of people a child knows offline, but also include friends of friends and others they have only met online.
- Instant Messaging - Some SNS, such as Facebook, have made chat features available to users.
- Pictures and Videos – Most SNS allow users to post a profile picture. Many also allow users to post photos and videos to an online “album.”
- Status Updates - Users post these short sentences to let the people on their friends list know their actions, feelings, and thoughts.
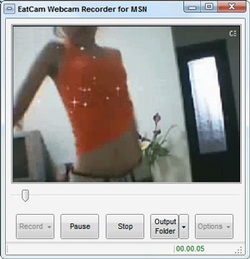
Webcams:
A webcam is a video camera connected to a computer. The camera may be an attachment or already installed in the computer. Webcam users can talk to each other through live streaming video or record videos to post on video-sharing sites, making webcams very useful tools for communication and for self-expression. Unfortunately, the extra exposure may also put children at greater risk of online victimization. If you decide to allow webcam use in your home, be aware of the risks so you can help your children use it more safely.
Creating Content Many children use their webcams to create videos which they post to video-sharing sites like YouTube and Vimeo. In these videos, children sing, dance, tell stories, share opinions, and show off other talents. While many are meant innocently, it is important that you talk to your children about what content you consider appropriate for posting online. For example, you may not want your children singing certain songs or using certain words. Make sure to review all videos before they are posted, and remind your children that their videos may be seen by a large audience. The videos may also be around for a long time; actions that seemed funny at age 14 may be embarrassing when they are adults applying for jobs.
Chatting Via Webcam Video-streaming sites like Justin.tv or Skype can be a great way to keep in touch with family and friends. With a webcam, users can connect with each other and engage in real-time, live video chats. Many people use these services to stay in touch with family members and friends. Some video chat services allow the content to be recorded, so it’s important to teach children to be mindful of what they say and do while chatting via webcam. Encourage them to report any inappropriate actions by other webcam users to you or the website immediately.
Manipulation by Predators Some predators try to take advantage of webcams’ capabilities in order to manipulate children. They may even send children webcams during the grooming process. While children may view the webcams simply as gifts, predators often use them to exploit children. They may start by making small, seemingly harmless suggestions, such as removing a shirt. If children comply, the suggestions may escalate to full nudity and sexual acts. If children stop cooperating, some predators will threaten to expose recordings they’ve made of the children’s previous actions in order to force them into complying.
A webcam is a video camera connected to a computer. The camera may be an attachment or already installed in the computer. Webcam users can talk to each other through live streaming video or record videos to post on video-sharing sites, making webcams very useful tools for communication and for self-expression. Unfortunately, the extra exposure may also put children at greater risk of online victimization. If you decide to allow webcam use in your home, be aware of the risks so you can help your children use it more safely.
Creating Content Many children use their webcams to create videos which they post to video-sharing sites like YouTube and Vimeo. In these videos, children sing, dance, tell stories, share opinions, and show off other talents. While many are meant innocently, it is important that you talk to your children about what content you consider appropriate for posting online. For example, you may not want your children singing certain songs or using certain words. Make sure to review all videos before they are posted, and remind your children that their videos may be seen by a large audience. The videos may also be around for a long time; actions that seemed funny at age 14 may be embarrassing when they are adults applying for jobs.
Chatting Via Webcam Video-streaming sites like Justin.tv or Skype can be a great way to keep in touch with family and friends. With a webcam, users can connect with each other and engage in real-time, live video chats. Many people use these services to stay in touch with family members and friends. Some video chat services allow the content to be recorded, so it’s important to teach children to be mindful of what they say and do while chatting via webcam. Encourage them to report any inappropriate actions by other webcam users to you or the website immediately.
Manipulation by Predators Some predators try to take advantage of webcams’ capabilities in order to manipulate children. They may even send children webcams during the grooming process. While children may view the webcams simply as gifts, predators often use them to exploit children. They may start by making small, seemingly harmless suggestions, such as removing a shirt. If children comply, the suggestions may escalate to full nudity and sexual acts. If children stop cooperating, some predators will threaten to expose recordings they’ve made of the children’s previous actions in order to force them into complying.



